How Plural can help you patch the latest CVE for ingress-nginx
This latest ingress-nginx vulnerability is a reminder that automated, compatibility-aware update pipelines aren’t just convenient - they’re essential for any team serious about production Kubernetes. And with Plural, you get them out-of-the-box.
Table of Contents
Let's face it - securing Kubernetes isn't getting any easier. Just last week, ingress-nginx (one of the most widely deployed Kubernetes ingress controllers) was hit with a series of critical vulnerabilities. The most severe of these (CVE-2025-1974) could potentially allow any workload in your cluster's internal pod network to exploit its admission webhook, ultimately revealing cluster secrets by leveraging flaws in how annotations are configured.
If you're running ingress-nginx in production right now, you're probably frantically trying to upgrade the controller. And you’ve probably encountered the dependency challenges that follow.
Upgrading third-party controllers
Kubernetes itself is rarely deployed alone - it's usually surrounded by a sprawling ecosystem of third-party components that vary wildly in quality and security posture. Upgrading these components isn't straightforward because they're tightly coupled with specific Kubernetes versions.
So for example, each version of ingress-nginx is designed to work with particular Kubernetes API versions. This means that right now, you might be caught between two bad options:
- Upgrade
ingress-nginxto patch the vulnerability, but risk breaking changes if your Kubernetes version is lagging behind - Force a Kubernetes upgrade first, potentially breaking other critical components in your cluster
How Plural solves the third-party controller upgrade problem automatically
Plural cuts this gordian knot. Our Observer resource does the following things:
- Regularly checks our internally maintained compatibility matrices to identify when new versions of components like
ingress-nginxare released. - Only suggests upgrades that are confirmed compatible with your specific Kubernetes versions.
This means that when a critical security patch like the recent ingress-nginx fix becomes available, the Observer automatically:
- Verifies the patch is compatible with your current Kubernetes versions
- Generates a precise pull request with the exact version changes needed
- Triggers your deployment pipeline to apply the changes safely
Here's a concrete example of how you'd configure this for the ingress-nginx vulnerability:
apiVersion: deployments.plural.sh/v1alpha1
kind: Observer
metadata:
name: ingress-nginx
spec:
crontab: "*/5 * * * *"
initial: 4.12.0
target:
order: SEMVER
type: ADDON # selecting our addon compatibility tables to poll
addon:
name: ingress-nginx # polling ingress nginx specifically
kubernetesVersions: # ensures the newest version we'd deploy
- "1.28" # is compatible with the given K8s versions in use
- "1.29"
- "1.30"
actions:
- type: PIPELINE
configuration:
pipeline:
pipelineRef:
name: ingress-nginx
namespace: infra
context:
name: ingress-nginx
version: $value
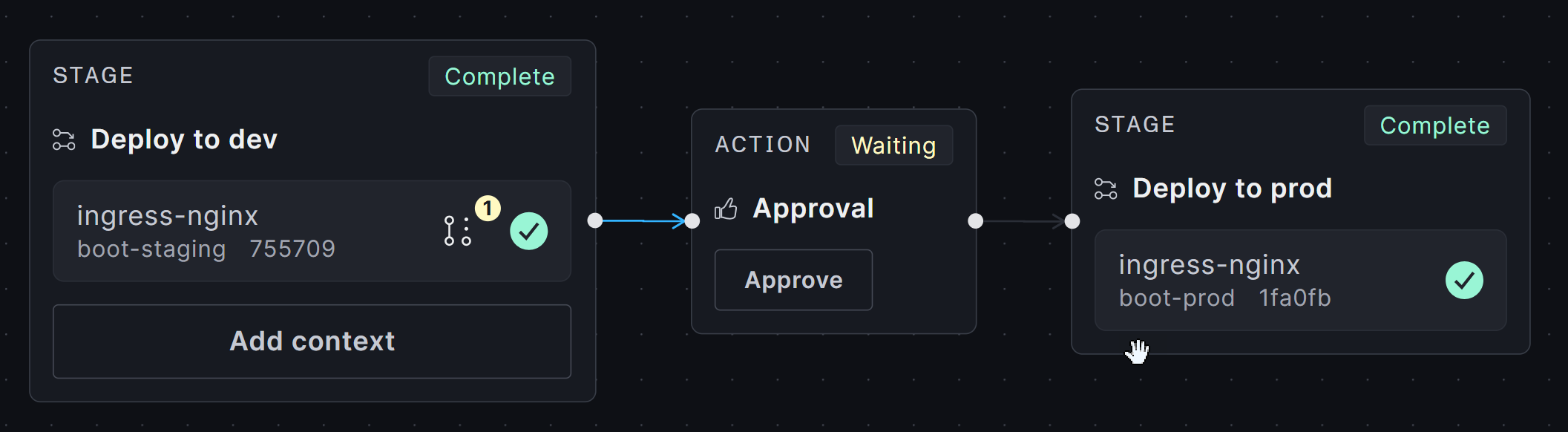
When a new compatible version is detected, the system automatically generates a PR with the necessary changes:
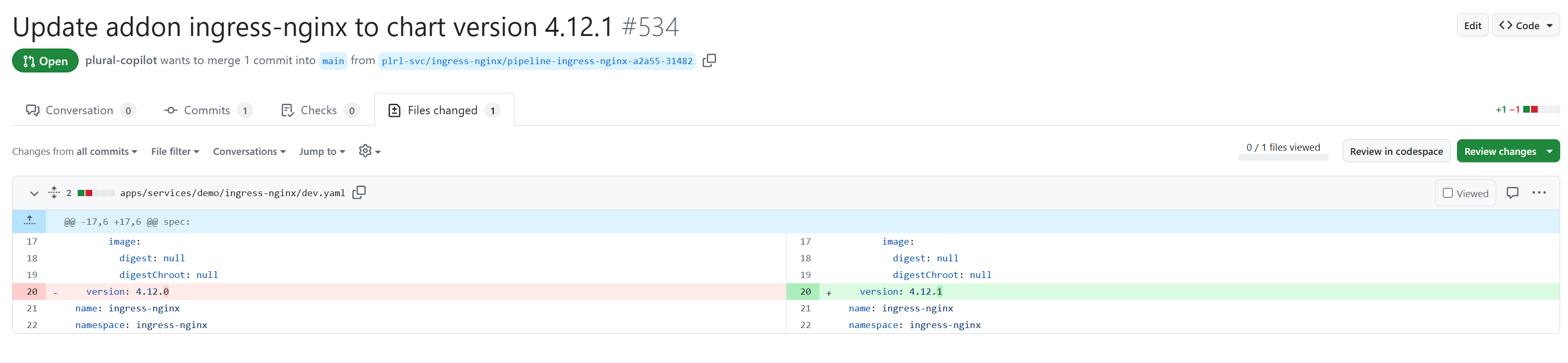
The resulting PR contains everything needed to safely update the component:
What makes this approach particularly powerful is that it's not just for one-off fixes. The Observer pattern can be applied to your entire Kubernetes ecosystem, ensuring that security patches are applied promptly across all components, updates never break compatibility with your existing infrastructure, and you can finally escape the dependency hell that comes with manual Kubernetes ecosystem management
Moving forward
This latest ingress-nginx vulnerability is a reminder that automated, compatibility-aware update pipelines aren’t just convenient - they’re essential for any team serious about production Kubernetes. And with Plural, you get them out-of-the-box.
Want to learn more about how Plural can help automate your Kubernetes security posture? Let us know - we're always looking for ways to make managing Kubernetes less painful and more secure.
Newsletter
Join the newsletter to receive the latest updates in your inbox.