
Kubernetes Ingress: The Ultimate Guide
Master Kubernetes Ingress with this comprehensive guide, covering key components, configurations, and best practices for efficient traffic management.
Table of Contents
In the dynamic world of Kubernetes, efficiently managing external access to your services is paramount. Kubernetes Ingress offers a powerful and flexible solution, acting as a single entry point for all incoming traffic.
This guide demystifies Kubernetes Ingress, clearly and concisely explaining its core concepts and practical implementation. We'll explore how Ingress controllers work, how to define routing rules, and how to implement essential security measures like SSL/TLS encryption. But Ingress isn’t just about configuration—it’s also about maintenance. As your environment scales, keeping Ingress controllers like ingress-nginx secure and compatible becomes increasingly challenging. That’s where Plural comes in. We will also explore how Plural keeps your Ingress layer patched, reliable, and secure—so you can focus on shipping, not firefighting.
Unified Cloud Orchestration for Kubernetes
Manage Kubernetes at scale through a single, enterprise-ready platform.
Key Takeaways
- Ingress streamlines traffic routing: Manage external access to your Kubernetes services efficiently with a single entry point and configurable rules, simplifying network complexity.
- Controller selection is critical: Evaluate popular Ingress Controllers like Nginx, Traefik, and HAProxy, considering factors such as performance, configuration complexity, and community support to choose the best fit for your needs.
- Optimize for security and performance: Secure your Ingress with HTTPS, implement appropriate load balancing, monitor key metrics, and establish robust troubleshooting procedures for a resilient and efficient setup.
What is Kubernetes Ingress?
Definition and Purpose
Kubernetes Ingress exposes your applications running inside a Kubernetes cluster to the outside world. Think of Ingress as a smart reverse proxy and load balancer for all your services. It acts as a single entry point for external traffic, routing requests to the appropriate services based on rules you define. You consolidate routing configurations within an Ingress resource instead of exposing each service individually with a LoadBalancer or NodePort. This simplifies network management and improves security. The Ingress resource itself doesn't handle the traffic; it provides instructions for the Ingress Controller.

Key Ingress Components
An Ingress resource is a Kubernetes object containing routing rules. These rules specify how different hostnames or URL paths should map to specific services within your cluster. For Ingress to work in your cluster, an Ingress Controller must be running. You must select at least one ingress controller and ensure it is set up in your cluster. Many Ingress Controllers are available, including the popular Ingress-Nginx and Traefik.
How Kubernetes Ingress Works
Traffic Routing Mechanisms
Kubernetes Ingress acts as a reverse proxy and load balancer for your cluster. It defines how external traffic reaches your internal Kubernetes services, which then connect to your pods. The Ingress resource provides the rules, and an Ingress Controller does the actual work of managing incoming requests based on that configuration. This separation allows flexibility and customization in managing external access to your applications.
Ingress Rules and Controllers
An Ingress Controller is essential. Without an Ingress Controller, your Ingress definitions are inert. You'll need to choose and install one. The Ingress resource uses rules to determine where incoming traffic goes. These rules, defined by developers, specify how to match incoming requests based on factors like hostnames and URL paths. The Ingress Controller uses these rules to route traffic to the correct services.
Kubernetes Ingress: Core Features and Benefits
Kubernetes Ingress offers several key features that streamline traffic management and enhance the security and availability of your applications.
Load Balancing
Ingress acts as a load balancer, distributing incoming traffic across multiple replicas of your application. This ensures high availability and prevents overload by spreading client requests among available pods. This distribution improves resource utilization and prevents any single pod from becoming a bottleneck. For applications experiencing fluctuating traffic patterns, Ingress controllers can dynamically adjust the load balancing to maintain optimal performance.
SSL/TLS Termination
Security is paramount, and Ingress simplifies implementing SSL/TLS encryption for your applications. Ingress can handle the encryption and decryption of traffic, offloading this computationally intensive task from your application pods. This improves performance and centralizes certificate management, making updating and maintaining your security posture easier. With Ingress managing SSL/TLS, your application code doesn't need to handle encryption directly, simplifying development and deployment.
Name-Based Virtual Hosting
Hosting multiple applications under a single IP address is a common requirement, and Ingress enables this through name-based virtual hosting. Ingress can route traffic to different services based on the requested hostname by leveraging HTTP host headers. This allows you to host multiple websites or applications with distinct domain names while sharing the same underlying infrastructure. This simplifies infrastructure management and reduces costs.
Path-Based Routing
Fine-grained control over traffic routing is achieved through path-based routing. Ingress allows you to define rules that direct traffic to specific services based on the URL path. This enables you to route requests to different versions of your application or different microservices based on the requested endpoint. For example, you could route /api/v1 requests to one service and /api/v2 requests to another, allowing for seamless versioning and updates. Combining path-based routing with other Ingress features like rewrites and redirects provides more sophisticated traffic management.
Getting Hands-On with Kubernetes Ingress
Let's get into the practical details of configuring Kubernetes Ingress. This section outlines setting up a basic Ingress resource, defining routing rules, and implementing SSL/TLS encryption.
Basic Ingress Resource Structure
A Kubernetes Ingress resource is defined as a YAML file. This file acts as a blueprint, instructing the Ingress Controller on how to route external traffic to your services. It's essentially a configuration template. An Ingress resource includes the following:
apiVersion: Specifies the API version for the Ingress object (e.g.,networking.k8s.io/v1).kind: Indicates the resource type, which isIngress.metadata: Contains metadata about the Ingress, such as its name and namespace.spec: This section defines the Ingress rules, including routing based on hostnames and paths. Thespecalso includes abackendsection for default routing. The Kubernetes documentation provides further details on Ingress resource structure.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: basic-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
spec:
ingressClassName: nginx-demo
rules:
- host: demo.example.com
http:
paths:
- path: /demo-path
pathType: Prefix
backend:
service:
name: demo
port:
number: 8080Define Routing Rules
Routing rules determine how incoming traffic is directed to different services within your cluster. These rules are defined within the spec section of the Ingress resource. Each rule typically consists of host and a set of paths. The host specifies the domain name or IP address for the rule. The paths section defines how traffic to specific URL paths should be routed. For example, you could route traffic to /api to your API service and traffic to /blog to your blog service. This allows you to manage traffic flow based on the URL structure.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: example-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
spec:
rules:
- host: example.com
http:
paths:
- path: /api
pathType: Prefix
backend:
service:
name: api-service
port:
number: 8080
- path: /blog
pathType: Prefix
backend:
service:
name: blog-service
port:
number: 80Implement SSL/TLS
Securing your Ingress with SSL/TLS encryption is critical for protecting data transmitted between clients and your services. This involves configuring your Ingress to use TLS certificates, either specified directly within the Ingress resource or by referencing secrets containing your certificate data through annotations. SSL/TLS ensures encrypted communication with your Kubernetes services, protecting sensitive information.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: sample-app-ingress
namespace: default
spec:
ingressClassName: nginx
tls:
- hosts:
- www.example.com
secretName: example-ingress-cert # Reference to the TLS secret
rules:
- host: "www.example.com"
http:
paths:
- pathType: Prefix
path: "/"
backend:
service:
name: sample-app-service
port:
number: 80Choosing the Right Kubernetes Ingress Controller
Choosing the right ingress controller is a critical decision that impacts performance, security, and maintainability.
Popular Ingress Controller Options
Several ingress controllers are available, each with its strengths and weaknesses. Here are a few popular options:
- Nginx Ingress Controller: One of the most widely deployed Kubernetes ingress controllers. Built on the robust Nginx web server, the Nginx Ingress controller is known for its performance and rich feature set.
- Traefik: Traefik emphasizes dynamic configuration and ease of use. Its automatic service discovery and integration with various backends make it well-suited for microservices architectures. Traefik simplifies complex routing and reduces manual configuration.
- HAProxy Ingress: When high performance and reliability are essential, the HAProxy Ingress Controller, based on the HAProxy load balancer, delivers. It provides advanced features for applications demanding high availability.
Choosing an Ingress Controller
Selecting the appropriate ingress controller depends on your specific requirements and infrastructure. Consider these factors:
- Ease of Configuration: Some controllers are more complex to configure than others. Choose a controller that aligns with your team's expertise.
- Performance: Performance needs vary by application. Benchmark different controllers to identify the best fit for your expected traffic.
- Community Support: A strong community offers valuable resources and support. Evaluate the community surrounding each controller.
- Compatibility: Ensure compatibility with your existing infrastructure, including your cloud provider and networking setup. A seamless integration simplifies deployment and ongoing management.
Advanced Ingress Configurations
Once you’ve grasped the basics of Kubernetes Ingress, you can leverage more advanced configurations to fine-tune your traffic management. These advanced features offer greater control over routing, security, and performance.
Customize with Annotations
Annotations provide a powerful mechanism to extend the functionality of your Ingress resources. These key-value pairs, added directly to your Ingress definitions, allow customization beyond the standard Ingress specification. For example, you can configure specific features of your Ingress controller, such as enabling sticky sessions, setting timeouts, or modifying load-balancing behavior.
Rewrite Rules and Redirects
Ingress rewrite rules offer a flexible way to manipulate incoming request paths before they reach your backend services. This is invaluable for maintaining backward compatibility with older URLs or implementing clean, SEO-friendly URL structures. You can rewrite paths based on regular expressions, allowing for complex transformations. Similarly, redirects enable you to seamlessly guide traffic from one URL to another, handling changes in your application's structure or implementing HTTP to HTTPS redirection.
Rate Limiting and Access Control
Protecting your services from abuse and ensuring fair usage is crucial. Rate limiting within your Ingress configurations allows you to control the number of requests per second or minute from specific clients or IP ranges. This helps prevent denial-of-service attacks and ensures your services remain available to legitimate users. Furthermore, access control mechanisms, often implemented through annotations or external authentication services, enable you to restrict access to your services based on various criteria, such as IP addresses, authentication tokens, or other custom rules.
Kubernetes Ingress Best Practices
After covering the core concepts and configurations of Kubernetes Ingress, let's discuss best practices for ensuring its security, performance, and maintainability. Implementing these practices will lead to a more robust and reliable Ingress setup.
Monitor and Troubleshoot
Implement comprehensive monitoring for your Ingress Controllers and backend services. Track key metrics such as request latency, error rates, and throughput. Set up alerts for critical events, such as Ingress Controller failures or high error rates. Effectively managing Ingress resources is key to ensuring reliable access to your services. Ingress-nginx supports a rich collection of Prometheus metrics. If you have Prometheus and Grafana installed on your cluster, then Prometheus will already be scraping this data due to the scrape annotation on the deployment. See Plural's guide on Kubernetes monitoring best practices.
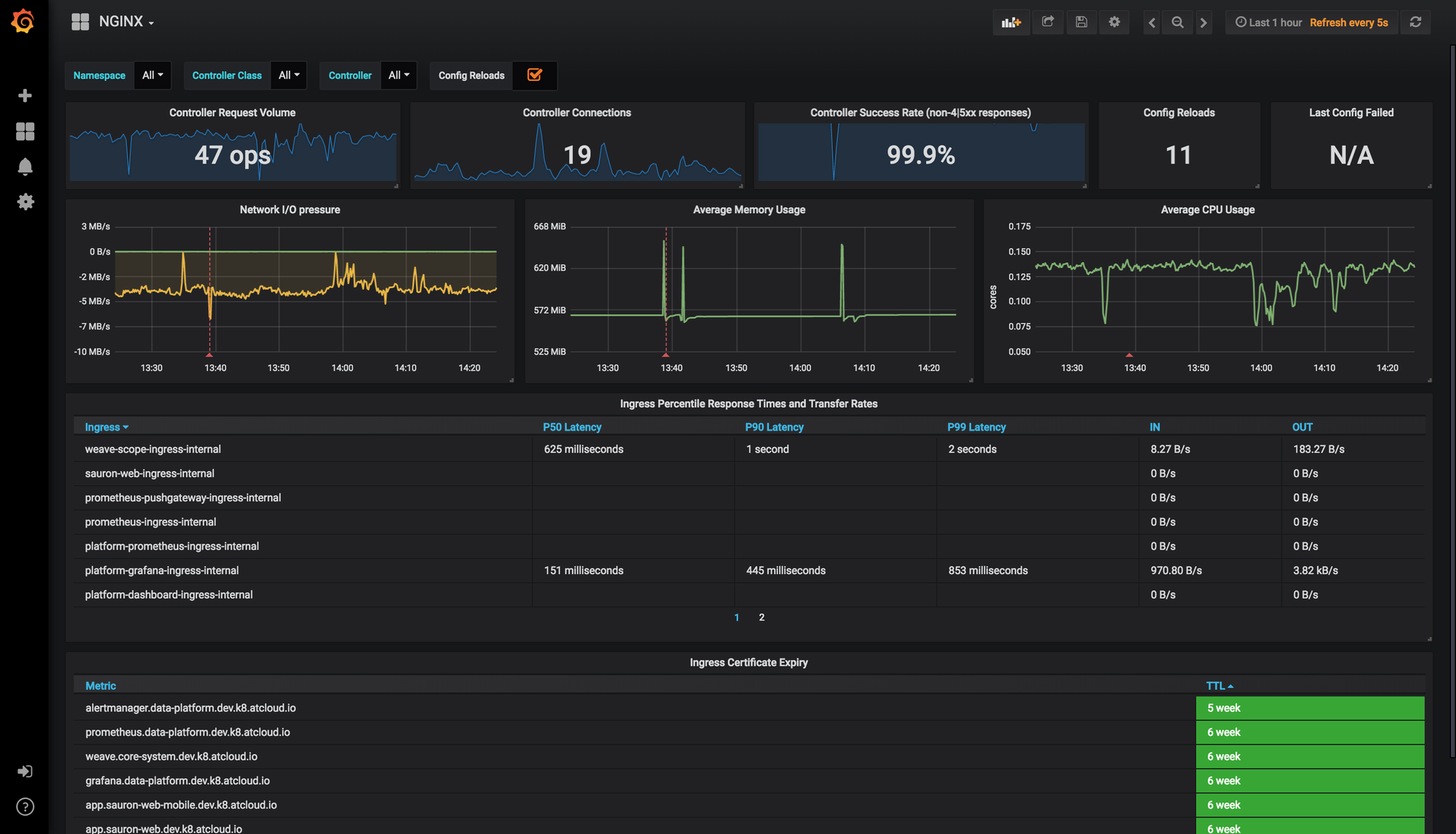
Security Considerations
Kubernetes is rarely deployed alone - it's usually surrounded by a sprawling ecosystem of third-party components that vary wildly in quality and security posture, such as Ingress controllers. Upgrading these components isn't straightforward because they're tightly coupled with specific Kubernetes versions.
The latest ingress-nginx vulnerability is a reminder that automated, compatibility-aware update pipelines aren’t just convenient - they’re essential for any team serious about production Kubernetes.
How Plural Automates Third-Party Controller Upgrades
This is precisely the kind of problem Plural is built to solve. Plural’s Observer resource automates the entire upgrade process for third-party components like ingress-nginx, removing the manual overhead and guesswork. It works by:
- Continuously monitoring Plural’s internally maintained compatibility matrices for updates to key components.
- Only surfacing upgrade recommendations are fully verified to be compatible with your specific Kubernetes versions.
So when a critical security patch—like the recent ingress-nginx fix—is released, Plural’s Observer steps in automatically to:
- Confirm the patch's compatibility with your current Kubernetes environment.
- Generate a pull request with the exact version changes required.
- Trigger your deployment pipeline to roll out the update safely.
Here’s what that looks like in practice for ingress-nginx:
apiVersion: deployments.plural.sh/v1alpha1
kind: Observer
metadata:
name: ingress-nginx
spec:
crontab: "*/5 * * * *"
initial: 4.12.0
target:
order: SEMVER
type: ADDON # selecting our addon compatibility tables to poll
addon:
name: ingress-nginx # polling ingress nginx specifically
kubernetesVersions: # ensures the newest version we'd deploy
- "1.28" # is compatible with the given K8s versions in use
- "1.29"
- "1.30"
actions:
- type: PIPELINE
configuration:
pipeline:
pipelineRef:
name: ingress-nginx
namespace: infra
context:
name: ingress-nginx
version: $value
Once a compatible version is detected, Plural automatically creates a pull request containing all the necessary changes to perform a safe, reliable upgrade.

The resulting PR contains everything needed to update the component safely:
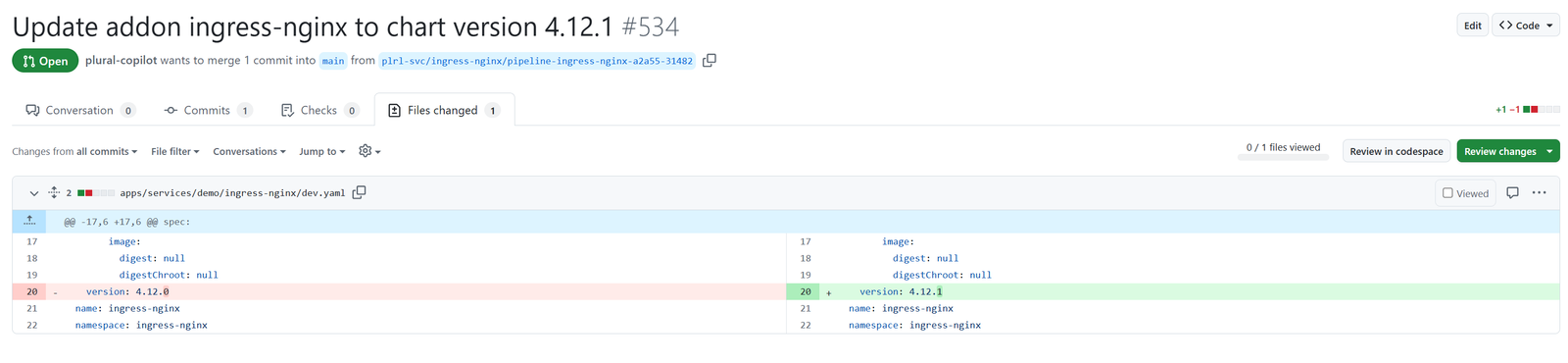
This approach is particularly powerful because it's not just for one-off fixes. The Observer pattern can be applied to your entire Kubernetes ecosystem, ensuring that security patches are applied promptly across all components, updates never break compatibility with your existing infrastructure, and you can finally escape the dependency hell that comes with manual Kubernetes ecosystem management
Want to learn more about how Plural can help automate your Kubernetes security posture? Let us know - we're always looking for ways to make managing Kubernetes less painful and more secure.
Related Articles
- Kubernetes Port Forwarding Essentials
- Kubernetes Cluster Security: A Deep Dive
- Mastering Kubernetes Taints: Best Practices
- Top tips for Kubernetes security and compliance
- Deep Dive into Kubernetes Service Types
Unified Cloud Orchestration for Kubernetes
Manage Kubernetes at scale through a single, enterprise-ready platform.
Frequently Asked Questions
Why should I use an Ingress controller instead of exposing my services directly?
An Ingress controller offers several advantages over directly exposing services via LoadBalancer or NodePort. It simplifies management by consolidating routing rules into a single resource. Ingress also typically provides additional features like SSL/TLS termination, URL rewriting, and advanced load balancing, reducing the complexity of your application's external access strategy. This centralized approach improves security and maintainability compared to managing individual service exposures.
How do I choose the right Ingress controller for my needs?
Selecting an Ingress controller depends on factors like ease of configuration, performance requirements, community support, and compatibility with your existing infrastructure. Nginx Ingress Controller is known for its performance and rich features. Traefik excels in the dynamic configuration and integration of microservices. HAProxy Ingress is a strong choice for high-availability scenarios. Evaluate your specific needs and the strengths of each controller to make an informed decision.
What are some common troubleshooting steps for Ingress issues?
Troubleshooting Ingress problems often involves verifying the Ingress resource definition for errors, checking the Ingress controller logs for clues, and testing connectivity directly to the backend service to isolate the source of the problem. Tools like kubectl describe ingress and kubectl logs can be invaluable during this process.
How can I secure my Ingress resources?
Securing your Ingress involves using HTTPS, regularly rotating SSL/TLS certificates, implementing strong authentication and authorization mechanisms, and using RBAC to control access to your Ingress resources. Regular security audits and penetration testing can further enhance your security posture.
How do I scale my Ingress to handle high-traffic loads?
Scaling Ingress involves choosing a horizontally scalable Ingress controller, optimizing resource allocation for controller pods, and implementing efficient load-balancing algorithms. Monitoring key metrics like request latency and error rates helps identify bottlenecks and optimize performance under heavy load.
Newsletter
Join the newsletter to receive the latest updates in your inbox.









