Best Practices for Kubernetes Security and Compliance
Since its launch in 2015, Kubernetes has become the leading platform for container orchestration. According to the 2023 CNCF Annual Survey, 84% of organizations use or explore Kubernetes in production. However, as adoption grows, so do the security challenges. Over 40% of users report security as a significant concern in their Kubernetes environments.
Why are security and compliance critical for Kubernetes deployments?
Both security and compliance are essential for the success and protection of Kubernetes deployments. Failing to address either can result in significant risks. The 2024 Red Hat Kubernetes Adoption, Security, and Market Trends Report highlights the impact of security issues:
- 53% experienced project delays due to security vulnerabilities.
- 46% faced revenue or customer loss from security incidents.
- 26% saw employee terminations linked to security breaches.
In addition, 30% encountered fines, legal actions, or lawsuits for failing to comply with regulations such as:
- FedRAMP: Ensures cloud services meet U.S. government security standards.
- GDPR: Protects the privacy of EU citizen’s data.
- HIPAA: Safeguards healthcare data in the U.S.
- CIS Kubernetes Benchmarks: Provides specific guidelines for securing Kubernetes clusters.
Ensuring both strong security and regulatory compliance is crucial for avoiding costly consequences, building customer trust, and ensuring the long-term success of Kubernetes deployments.
The Security Challenge: Managing Third-Party Software in Kubernetes
Kubernetes’ flexibility is one of its greatest strengths, but it also introduces significant security challenges—especially regarding third-party software. Most Kubernetes deployments rely heavily on external controllers, operators, and services. While these components extend functionality, they also expand the attack surface.
A typical scenario highlights the issue: an enterprise sets up a CVE scanner in its Kubernetes cluster, only to be flooded with hundreds of critical vulnerabilities. Often, these stem from open-source projects that use outdated or insecure base images—like an older Debian release riddled with known vulnerabilities. These issues aren’t always intentional, but they can have serious consequences.
Consider the Log4Shell vulnerability (CVE-2021-44228), which emerged in December 2021. This critical flaw in the widely-used Log4j library affected numerous organizations, including major companies like Apple, Amazon, and Tesla. Attackers exploited this vulnerability to execute arbitrary code, potentially compromising entire systems. This incident highlighted how third-party software can introduce serious risks, even when Kubernetes is adequately secured.
The real challenge lies in understanding the blast radius of these vulnerabilities. When a third-party component is compromised, the entire cluster is at risk. This makes managing third-party software a high-stakes task that requires careful oversight.
Current Approaches and Their Limitations
Securing Kubernetes clusters is tough, and how most teams handle it today doesn’t make it any easier. Here are some of the common approaches and why they fall short:
1. Manual Security Updates Across Kubernetes Clusters
Many teams still update Kubernetes clusters manually. This approach might work for a small setup, but it falls apart as soon as you have multiple Kubernetes clusters. It’s slow, tedious, and easy to miss something critical.
2. Inconsistent Security Policies
When different teams manage different Kubernetes clusters, security policies often become inconsistent. One cluster might have strict rules, while another is left wide open. This inconsistency creates vulnerabilities and makes compliance a nightmare.
3. Hard-to-Coordinate Updates
In larger organizations, multiple teams work on different parts of the system. Coordinating updates across these teams is tricky, and delays are common. This means some Kubernetes clusters stay unpatched longer than they should.
4. Delays in Security Patches
Even when a patch is available, deploying it takes time. You need to test it, ensure it doesn’t break anything, and then roll it out. During this time, your system is vulnerable, which is what attackers look for.
These challenges clarify that organizations need a more efficient and automated solution for managing Kubernetes security. This is where the Plural comes in.
How Plural Solves Kubernetes Security Challenges
Securing Kubernetes isn’t easy—it’s a complex system with many moving parts. You must manage updates, enforce security policies, and handle vulnerabilities while ensuring everything runs smoothly across Kubernetes clusters.
Plural simplifies these tasks with features designed to make Kubernetes security more manageable and effective. Here’s how:
Software Update Management
Plural makes managing control plane updates straightforward with its features, such as pre-flight checks and global services.
Pre-Flight check
Before performing an upgrade, Plural runs pre-flight checks to ensure the new Kubernetes version is compatible with your existing controllers and add-ons. This helps avoid issues that could arise from incompatible versions.
This Pre-Flight checkup consists of three steps:
-
API Deprecation Checks
Plural identifies APIs slated for removal using two methods:-
GitOps Integration: Plural integrates with your GitOps workflows to flag deprecated resources directly in your manifests. For instance, if your manifest includes a PodSecurityPolicy that will be removed in Kubernetes v1.25, Plural highlights this and suggests the updated API to use.
-
Cloud Provider Exports: Plural scrapes exports from cloud platforms like AWS to detect processes that might rely on deprecated APIs.
-
-
Controller Compatibility
Controller updates often lag, leading to compatibility issues. Plural tackles this by scraping release notes and documentation to map add-on versions to their compatible Kubernetes versions.Below is the version matrix generated by Plural by scraping the documentation for each controller. This matrix indicates which controller versions are compatible with specific Kubernetes versions. If a version is incompatible, it is flagged as blocking.
-
Add-On Mutual Compatibility(under development)
This feature will detect compatibility issues between controllers themselves. This will help prevent API conflicts and ensure all cluster-level services interact harmoniously after an upgrade.
Global Services
Plural's Global Services feature allows you to replicate services across your Kubernetes fleet, making it easier to manage low-level system add-ons like ingress controllers, service meshes, and cert managers. By defining a source service and using the GlobalService CRD, you can ensure consistent deployment and updates across multiple Kubernetes clusters. This helps maintain uniformity and simplifies shared services management across your infrastructure, ensuring updates are applied seamlessly to all relevant Kubernetes clusters.
For example, in the screenshot below, we set up the K3s system upgrade controller on a single cluster and replicated it using the GlobalService CR to all Kubernetes clusters with the edge: fabric tags.
For more details, check out the Global Services documentation.
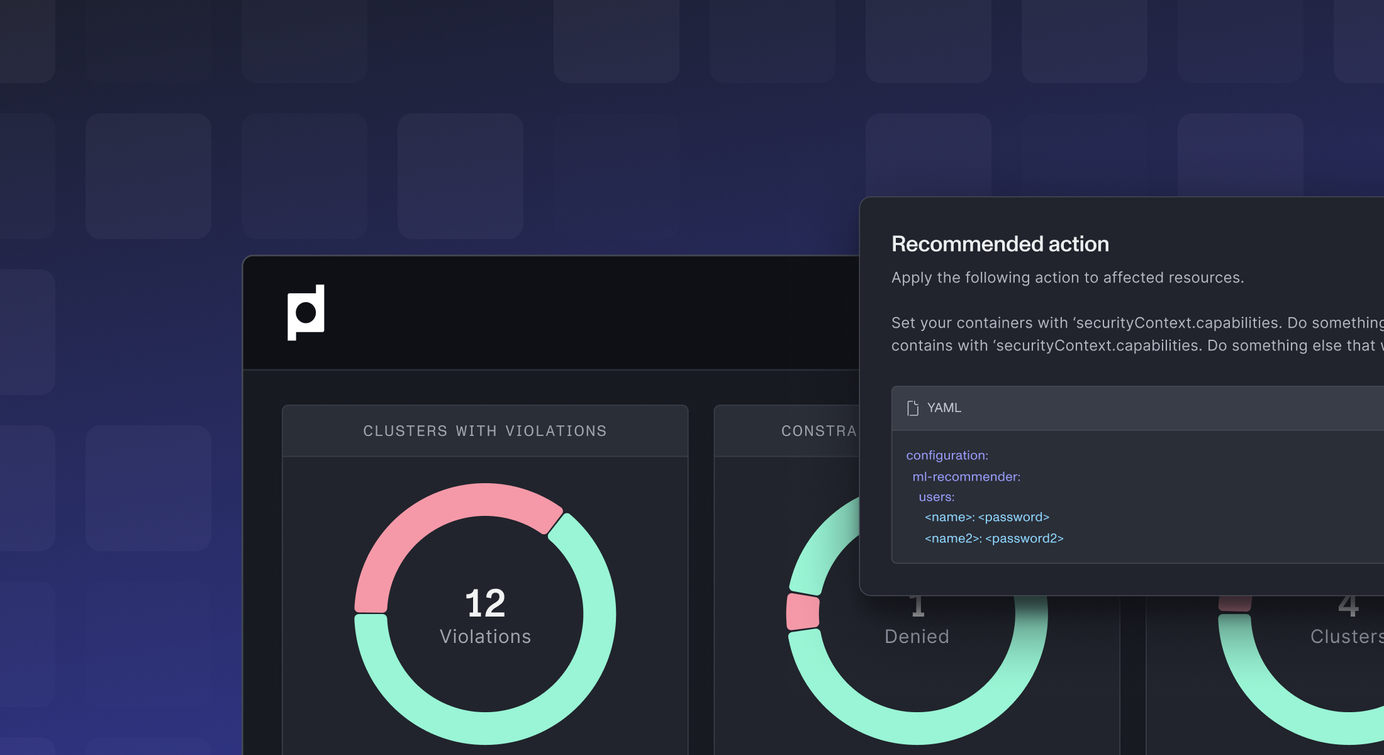
Policy Enforcement with OPA Gatekeeper
OPA Gatekeeper is a Kubernetes admission controller that uses the Open Policy Agent (OPA) to enforce policies on Kubernetes resources.
With Plural, managing OPA Gatekeeper is straightforward. The UI gives a clear overview of your policies, allowing you to see what’s being enforced in real time across your infrastructure. Plural’s self-service PR automation makes it simple to roll out Gatekeeper across your entire setup with minimal hassle.
OPA Gatekeeper enforces a variety of security best practices, such as:
- Enforcing read-only root filesystems for containers.
- Ensuring containers run as non-root users.
- Requiring network policies on every service.
- Enforcing resource limits (CPU and memory) for containers.
- Disallowing privileged containers to reduce security risks.
- Ensuring namespaces are correctly labeled for management and security.
- Restricting containers to trusted image registries only.
- Limiting container capabilities to reduce the attack surface.
- Preventing containers from using host networking.
- Enforcing pod security policies to avoid risky configurations.
- Ensuring sensitive data like passwords and tokens are managed securely.
- Audit logging is required to track actions for compliance and security.
- Enforcing specific Kubernetes versions to prevent outdated or unsupported versions.
If a resource doesn’t follow these rules, the Gatekeeper blocks it before it can cause trouble. This level of policy enforcement is a game-changer for Kubernetes, where configuration drift can easily lead to security risks.
Runtime governance is no small feat in Kubernetes, but OPA Gatekeeper makes it easy to lock down your environment and automatically ensure best practices are followed. With Plural, this process becomes even more seamless, giving you the peace of mind that your Kubernetes clusters are secure and compliant every time.
CVE Detection and Management
One of the most critical aspects of maintaining a secure cluster is staying on top of CVEs (Common Vulnerabilities and Exposures). With Plural, we’ve made it easier to manage these vulnerabilities by providing comprehensive CVE detection and visualization tools.
Plural aggregates CVE scans across your Kubernetes clusters, allowing you to see which Kubernetes clusters are affected and the criticality of each vulnerability. This gives you a clear view of where the risks lie and helps you prioritize remediation efforts based on severity.
With Plural’s CVE visualization interface, you can quickly identify:
- Which Kubernetes clusters have CVEs, and what is their criticality?
- Trends in vulnerabilities over time, helping you spot patterns.
- Vulnerabilities across different services and components.
By centralizing CVE data and making it easy to visualize, Plural helps you stay proactive about security, ensuring you can address critical vulnerabilities before they become a bigger problem. It’s a key part of maintaining a secure, compliant Kubernetes environment.
Plural Architecture: Security by Design
Architecture matters when securing any application, and Plural’s design is no exception. It is built with security in mind, making it easier to manage your Kubernetes clusters while minimizing exposure to potential risks.
Plural has a very efficient architecture consisting of two components: a control plane installed on the Kubernetes management cluster and a deployment agent installed on workload clusters. In each cluster, a Plural agent is run as a pod. All network communication within the platform is unidirectional, meaning traffic flows only from the managed Kubernetes clusters to the control plane. This approach ensures that your Kubernetes clusters can stay within secure environments, isolated from public networks, while still being manageable at scale.
The agent uses local credentials to apply changes, eliminating the need to centralize credentials in a global controller. This reduces the risk of a single point of failure or attack vector, keeping your credentials safe and ensuring that no sensitive information is exposed unnecessarily.
This architecture also makes it easier to maintain compliance with strict standards like FedRAMP. FedRAMP compliance focuses heavily on managing network perimeters, and Plural’s approach to network security aligns perfectly with these requirements. With no ingress allowed into the perimeter and controlled egress, you can be confident that your Kubernetes clusters remain secure and compliant, all while being easy to manage at scale.
Conclusion
Securing Kubernetes is a complex task, but it becomes much more manageable with the right tools. Plural simplifies Kubernetes security by offering robust solutions like automated cluster and controller updates, policy enforcement with OPA Gatekeeper, and comprehensive CVE detection and management. These features help you stay on top of security, ensuring your Kubernetes clusters are up-to-date, compliant, and protected from vulnerabilities.
By automating key security processes, Plural reduces the risk of human error and makes it easier to scale security across multiple Kubernetes clusters. The long-term benefits are clear: fewer vulnerabilities, less downtime, and a more secure, compliant environment. With Plural, you can focus on building and deploying applications, knowing that your Kubernetes security is in good hands.
Ready to secure your Kubernetes clusters? Get started with Plural today and experience a seamless, secure, and compliant Kubernetes environment.
Newsletter
Join the newsletter to receive the latest updates in your inbox.